I am a software security researcher and entrepreneur. My research interests primarily revolve around AI and Software Supply Chain Security.
I am currently a Scientist in the Cybersecurity group at the Qatar Computing Research Institute. Previously, I was an Assistant Professor in the CSE Department at Chalmers University of Technology and the University of Gothenburg. Prior to that, I was a Scientist at the University of Wisconsin–Madison, where I had the privilege of working with Prof. Somesh Jha and Prof. Thomas Reps on software debloating and machine learning robustness.
I completed my PhD in Computer Engineering at the University of Nebraska-Lincoln, where I was fortunate to work with Dr. Hamid Bagheri and Dr. Qiben Yan and obtained MSc in Computer Security from the University of Kent. I received ACM SIGSOFT distinguished paper award and (ISC)2 graduate scholarship.
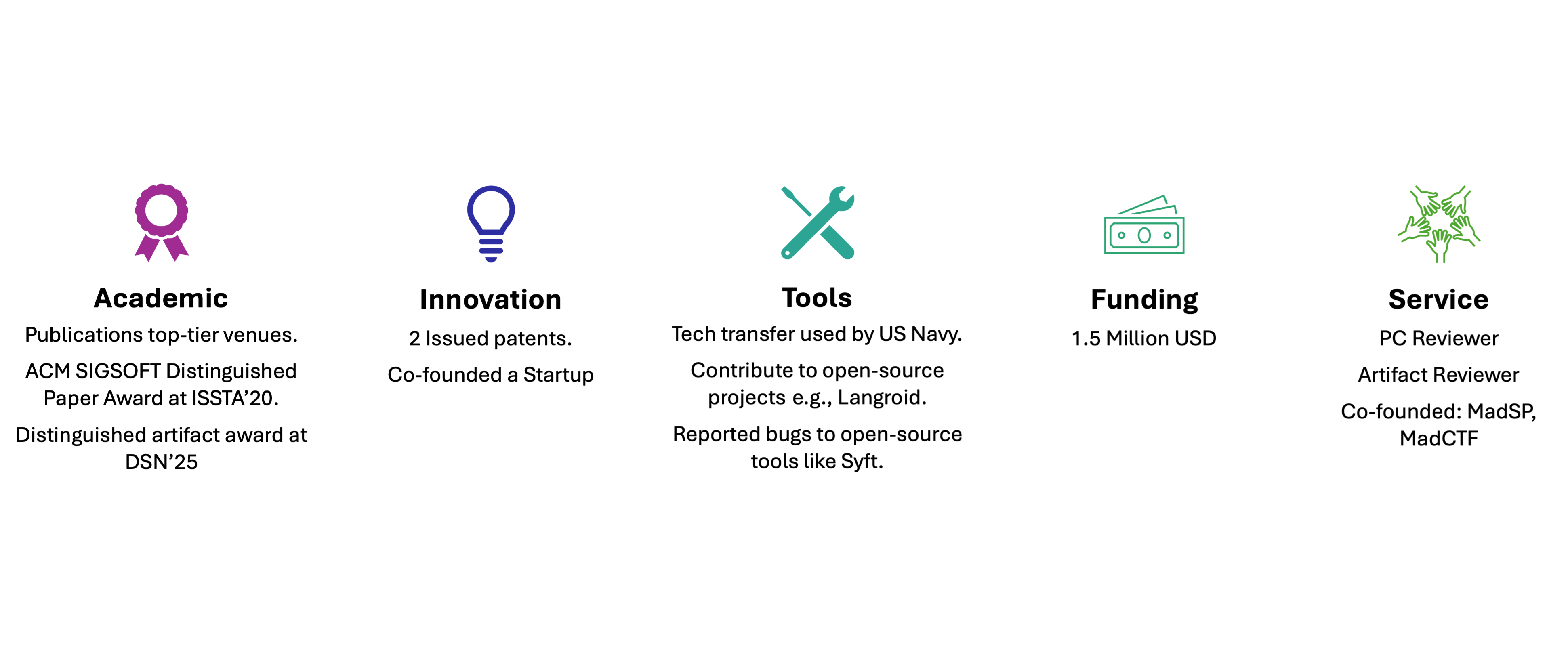
Research Impact at a Glance
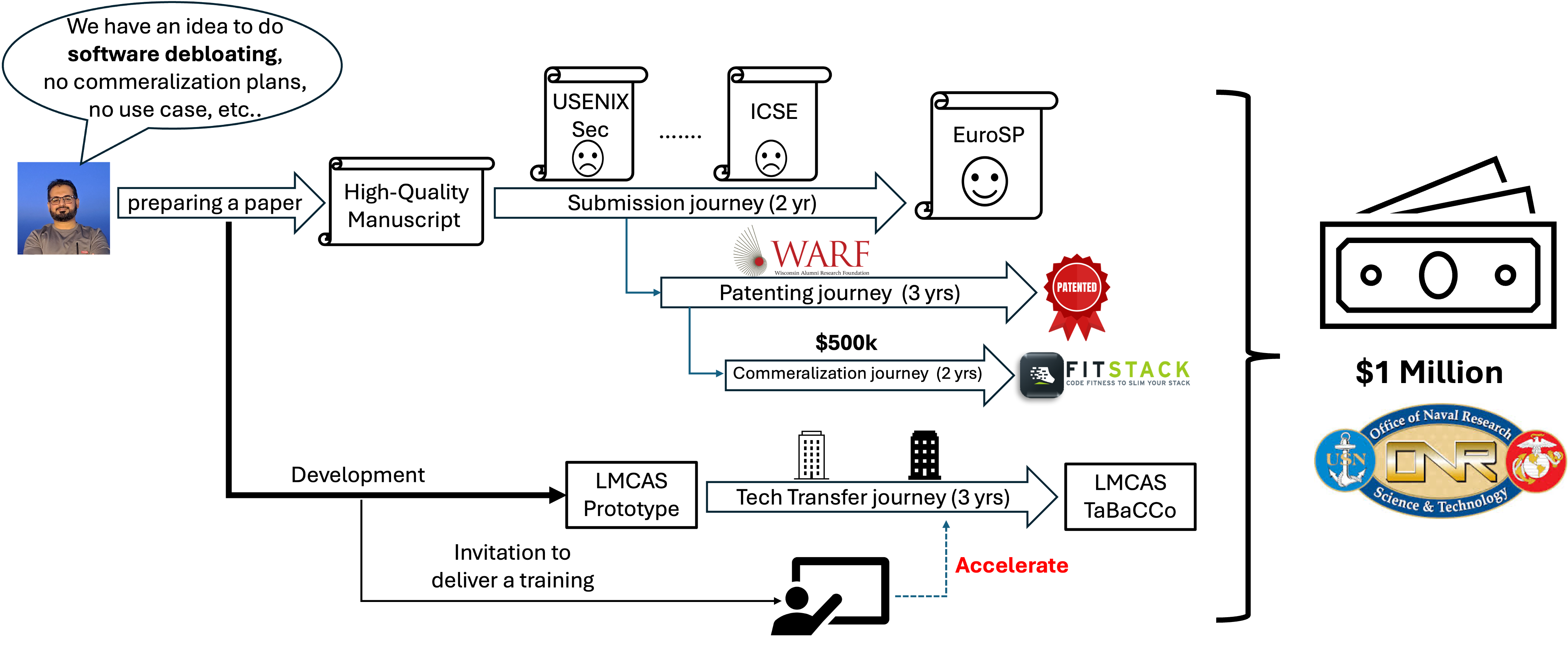
Innovation Journey: From idea to real-world impact
My work extends beyond academic publications to real-world implementation and impact. I have secured over $1.5 USD million in research and commercialization funding, co-founded a startup (FitStack), and had my research tools accepted for tech transfer by the Office of Naval Research (ONR). I hold two issued patents in software and data minimization, and actively release open-source artifacts to support reproducibility and community adoption. I’m passionate about supporting the OSS community by contributing to open-source projects such as Langroid and reporting critical issues in widely-used software supply chain tools like Syft.
Research Areas:
-
IoT Safety and Privacy: [USENIX’22, IEEE TSE’22, ISSTA’20]
-
Software Debloating: [EuroS&P’22, SIGMETRICS’24, FEAST’24]
-
Agentic AI Apps: [NeurIPS’24 OWA, DSN’25, EMSE’25]
-
AI/ML Robustness: [NeurIPS’22]
-
Android Security: [IEEE TIFS’20, INFOCOM’19]
View detailed research projects →
Academic Service:
- I served as a reviewer and external reviewer in the following conferences and journals: S&P’26, CCS’24, Euro S&P’22, USENIX’21, CSF’21, IEEE BigData’20, TIFS’20, TrustCOMM’20, INFOCOMM’17/18, IEEE Cloud Computing 2017, IEEE WCNC 2017.
- Postdoc representative in the Postdoc Advisory Committee (Academic Year 2021-2022)
- Graduate Students’ representative in the faculty committee (Academic Year 2016-2017)
- Graduate students’ representative in the Computer Engineering Committee (Academic Year 2017-2018)
Recent news:
- [Feb 2026] 🔥 Our paper "BACFuzz: Exposing the Silence on Broken Access Control Vulnerabilities in Web Applications" has been accepted to DIMVA'26
- [Nov 2025] 🔥 I discovered a critical bug in "Syft SBOM generation tools"
- [July 2025] 🔥 I started my appointment as a Scientist at Qatar Computing Research Institute
- [June 2025] 🔥 Our paper "An Empirical Evaluation of Pre-trained Large Language Models for Repairing Declarative Formal Specifications" has been accepted to EMSE'25
- [May 2025] 🔥 Our DSN'25 paper received Distinguished Artifact Award
- [April 2025] 🔥 I was invited to serve on the S&P'26 PC
- [Mar 2025] 🔥 Our paper "Towards More Dependable Specifications: An Empirical Study Exploring the Synergy of Traditional and LLM-Based Repair Approaches" has been accepted to DSN'25
- [Jan 2025] 🔥 I started my appointment as an Assistant Professor at Chalmers University and University of Gothenburg
- [Oct 2024] 🔥 Our paper "DepsRAG: Towards Agentic Reasoning and Planning for Software Dependency Management" has been accepted to (NeurIPS'24 Workshop on Open-World Agents)
- [Sept 2024] 🔥 Our patent application "Computer Implemented Program Specialization" has issued.
- [Aug 2024] 🔥 Our papers "SoK: Software Debloating Landscape and Future Directions" and "Software Debloating from Exception-Handler Lenses" have been accepted to (FEAST'24)
- [Jan 2024] 🔥 I implemented and released Python Dependency Chatbot. This chatbot is a RAG application over Knowledge Graph. Check out my blog for more info
- [Jan 2024] 🔥 Our patent application "Method and Apparatus for Improved Security in Trigger Action Platforms" has issued.
- [Dec 2023] 🔥 I was invited to serve on the CCS'24 TPC Software Security Track
- [Dec 2023] 🔥 Our paper "Machine Learning Systems are Bloated and Vulnerable" has been accepted to (SIGMETRICS'24)
- [Nov 2023] 🔥 Our ONR grant to `Holistic Debloating in the Age of LLM Technology`, is funded. Thank you, ONR!!!
- [July 2023] 🔥 We released Langroid, a framework to support developers to build Multi-agent LLM applications.
- [June 2023] 🔥🔥 ONR decided to open source the Tech Transferred version of our debloating tools LMCAS and SLASH.
- [June 2023] 🔥 I served on the Artifact Evaluation Committees for NDSS'24 and CGO'24
- [Dec 2022] 🔥 Our paper "autoMPI: Automated Multiple Perspective Attack Investigation with Semantics Aware Execution Partitioning" has been accepted to (TSE).
- [Sept 2022] 🔥 Our paper "Robust Learning against Relational Adversaries" has been accepted to (NeurIPS'22)
- [June 2022] 🔥 Our paper "IoTCOM: Dissecting Interaction Threats in IoT Systems" has been accepted to (TSE)
- [Feb 2022] 🔥 Our paper "Lightweight, Multi-Stage, Compiler-Assisted Application Specialization" has been accepted to (Euro S&P'22)
- [July 2021] 🔥 Our tool "Lightweight, Multi-Stage, Compiler-Assisted Application Specialization" has been accepted for Tech Transfer by ONR.
- [July 2021] 🔥 Our paper "Practical Data Access Minimization in Trigger-Action Platforms" has been accepted to (USENIX'22)
- [May 2021] 🔥 Patent filed COMPUTER IMPLEMENTED PROGRAM SIMPLIFICATION
- [Feb 2021] 🔥 Patent filed A METHOD AND APPARATUS FOR IMPROVED SECURITY IN TRIGGER ACTION PLATFORMS
- [Aug 2020] 🔥 Our paper "Comparing formal models of IoT app coordination analysis" has been accepted to (SEAD'20).
- [April 2020] 🔥 Our paper "Scalable Analysis of Interaction Threats in IoT Systems" (ISSTA'20) received ACM SIGSOFT Distinguished Paper Award
- [Dec 2018] 🔥 Our paper Detecting Vulnerable Android Inter-App Communication in Dynamically Loaded Code" has been accepted to (INFOCOM'19)
- [Mar 2018] 🔥 Our paper "Efficient Signature Generation for Classifying Cross-Architecture IoT Malware" accepted to IEEE Conference on Communications and Network Security 2018.
- [Feb 2018] 🔥 Our paper "Towards Best Secure Coding Practice for Implementing SSL/TLS" has been accepted to MobiSec 2018 (INFOCOM)
Last updated: February 2026
